Warning : This Post Will Totally Kick Your Ass. If You Like This Post And/Or Have A Big Penis, Please Like Us On Your Favorite Social Networking Site !
 Would you Like to Buy WEED,Cocaine,Guns etc? Hire an Assassin Or Hacker to destroy somebody you loathe ? What if we told you its possible, and the thing that can do it is probably sitting in your lap right now.
Would you Like to Buy WEED,Cocaine,Guns etc? Hire an Assassin Or Hacker to destroy somebody you loathe ? What if we told you its possible, and the thing that can do it is probably sitting in your lap right now.
Welcome to the DEEP WEB ! The hangout of Assassins, hackers, drug dealers and pedophiles. Although it common understanding that you should not mess with these peoples, But it wouldn't hurt to take a peek, would it ?
The Basics To Deep Web :
In recent research it was discovered that only 0.03% of data is available to common web users. Common Search Engines like Google etc only search what is called Surface Web. The so-called Deep web is what your normal search engine can't access. The size if deep web is believed to be 7.5 Petabytes, about 5000 times larger than surface web.The dark Web is a bit like the Internet Secret Weapons Inventory. It's private. It's anonymous. It's powerful. It unleashes human nature in all its forms, both good and bad.
So here is what you need to access Deep Web :
Things You Need :
- TOR Client For Your PC. Link
- Working Firewall.
- If possible Linux.
- Some Common Sense.
What Is Deep Web ?
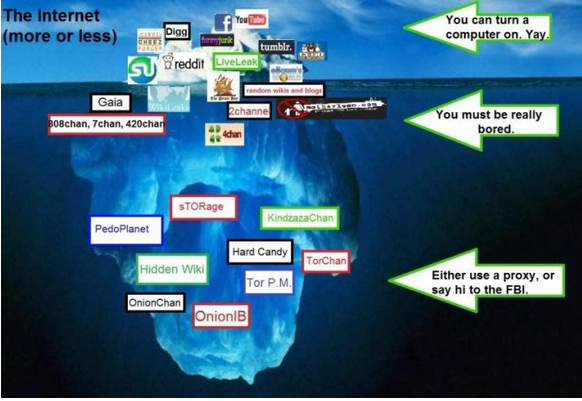 The term "Deep Web" was coined by Mike Bergman, founder of Bright Planet. Some people mistake Deep Web with Dark Web, Dark web stands for the computers that can no longer be reached via the Internet. It's a little part of Deep Web. As defined by Wikipedia : Deep Web is a haven for serious criminality.
The term "Deep Web" was coined by Mike Bergman, founder of Bright Planet. Some people mistake Deep Web with Dark Web, Dark web stands for the computers that can no longer be reached via the Internet. It's a little part of Deep Web. As defined by Wikipedia : Deep Web is a haven for serious criminality.
Deep web is also useful for whistle-blowers and undercover spies. It is believed that Edward Snowden, The whistle blower of NSA Prism program used deep web to leak official government documents.
Deep web means complete freedom and un-compromised security. It is not monitored by NSA or any other agency.
Forget .com, The .onion is here :
Deep web uses .onion domains, instead of popular .com. Reason is .onion A pseudo-top-level domain. pseudo-top-level domain are the one who do not participate in the world-wide official Domain Name System. That is why Google is unable to find sites these because the are not based on DNS system. .onion Offers complete anonymity and it's the first choice of any person doing illegal things. Also .onion domains are bound to only accept incoming traffic coming from TOR.Why Use TOR Instead Of Your Favorite Browser ?
 Data in the Deep Web is hard for search engines to see, but unseen doesn't equal unimportant. Most (deep web) websites are based to stay well hidden to a normal Google user. This is where TOR comes in, TOR aka The Onion Router routes your information through several routers in the world and enables you to see the hidden websites. For Example, You buy a pound of weed from deep web, and the DEA wants to arrest you, the cannot find you because your data is being routed through several routers around the world.
Data in the Deep Web is hard for search engines to see, but unseen doesn't equal unimportant. Most (deep web) websites are based to stay well hidden to a normal Google user. This is where TOR comes in, TOR aka The Onion Router routes your information through several routers in the world and enables you to see the hidden websites. For Example, You buy a pound of weed from deep web, and the DEA wants to arrest you, the cannot find you because your data is being routed through several routers around the world.Now Let's Access The Deep Web :
Assuming you have installed TOR on your computer, now open it and go to the onion icon, Click on the 'New Identity' button and you are good to go. Remember not to use any sites that you have stored your personal stuff in, Like Gmail. And make sure to get new identity every-time you start a new session. Also disable Javascript just in case something wrong happens.
Goodbye Google, Hello Hidden Wiki :
Searching deep web for quality information could be hard at first since it does not support your favourite search engine, But a good place to start is The Hidden Wiki, it is a place where every deep web url is submitted. Head over there now are lets start having some fun.
Link To Hidden Wiki : http://zqktlwi4fecvo6ri.onion/wiki/index.php/Main_Page
Lets Browse The Web :
Hire a Sharp Shooter, Or A private army, Ask White Wolves :
Want Something, Don't Have Money ? Message Dangler :
Want to buy weapons cheap ? Contact These Hard-asses :
http://silkroad3og4b6bq.onion/
Hackers For Hire :
2ogmrlfzdthnwkez.onion/
2ogmrlfzdthnwkez.onion/
If you need any more, Post a comment below and i'll get back at you. Also please notice that Deep Web uses Bitcoins as a currency, So try to get it if you want to get something.
So how was this post ? Love/Hate/Spot a mistake ? Please leave your comments and questions below and don't forget to like us us facebook, google+ and twitter. Thank You !
Sharing under RHP policy. It's a learning post. Do it at your own risk. We are not responsible for any of your trouble.






